Skip to main content
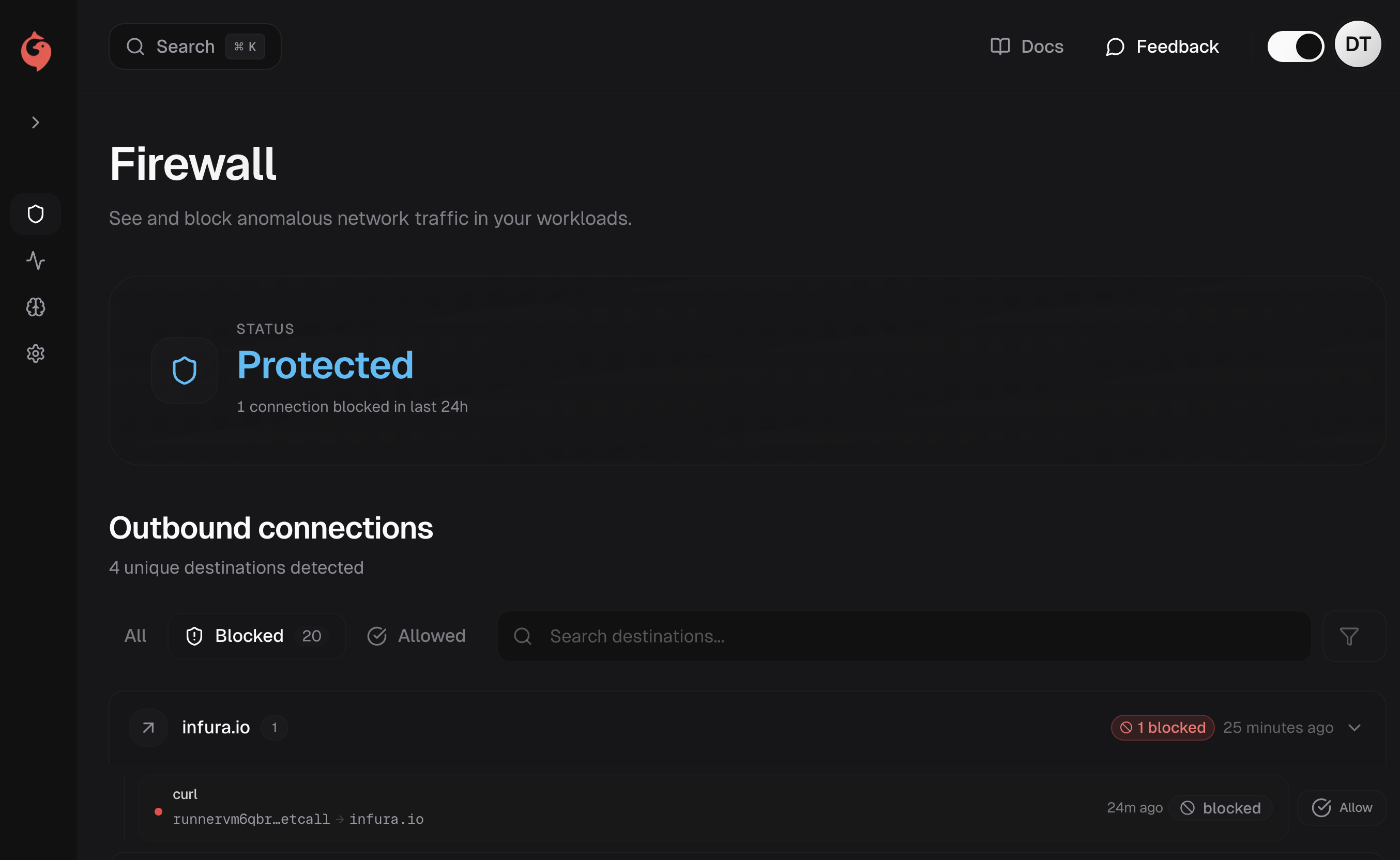
Garnet blocks connections to external destinations in real-time (C2 servers, crypto miners, supply chain threats, known malicious domains). When an agent observes an outbound connection to a blocklisted domain, the packet is dropped at the kernel level.
Incident Details
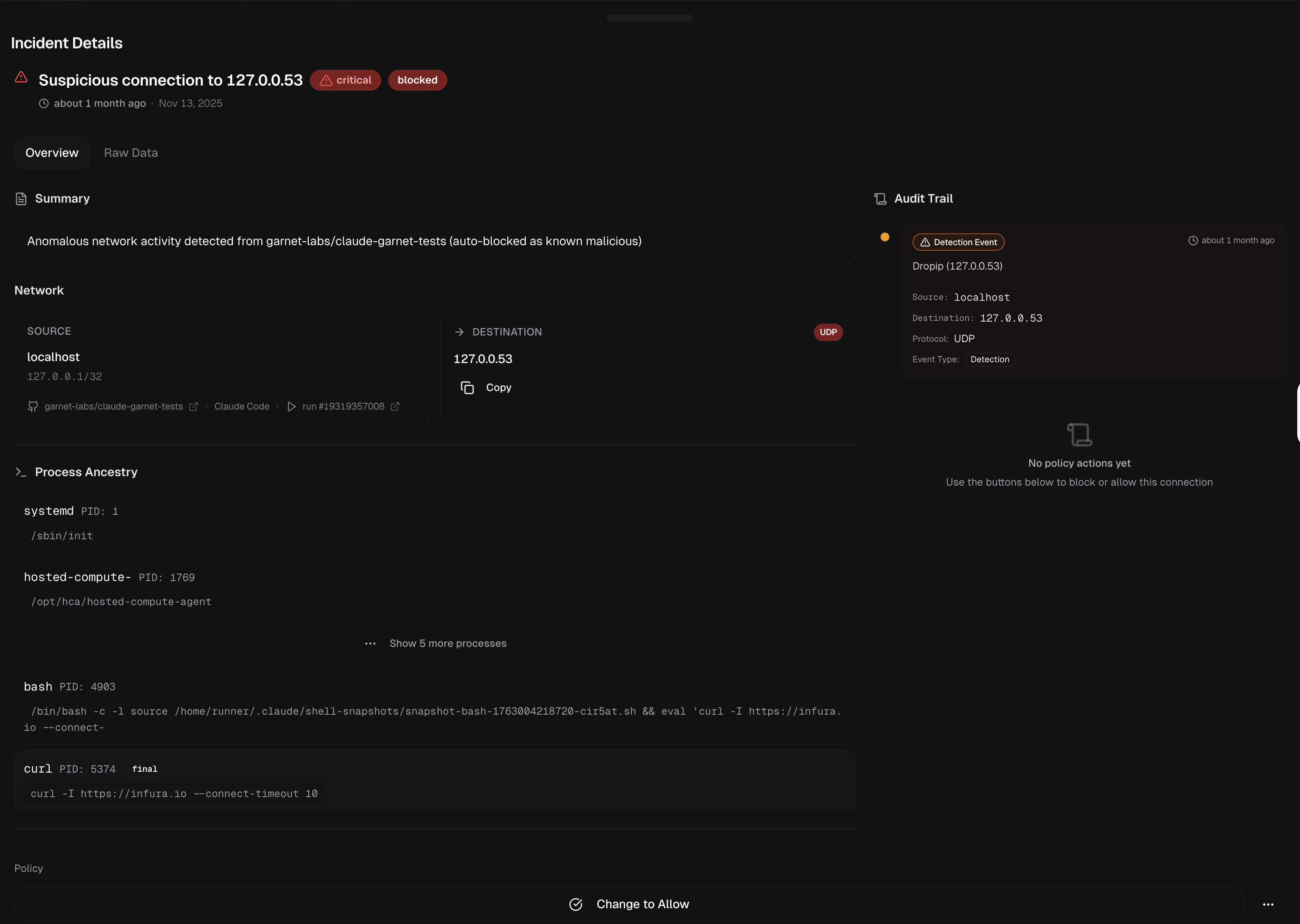
Each blocked connection includes full context: source, destination, event type, and complete process ancestry tree. Use the audit trail to understand exactly what triggered the block and trace it back through the process chain.
Network Policies
Garnet ships with managed network policies powered by our threat intelligence—curated blocklists of malicious domains maintained by our security team. Updates automatically. No configuration required.
You can also use network visibility to enrich and inform your own firewall rules.
If you’re deploying on Kubernetes and want to provide a policy YAML file to the agent, see Kubernetes → Advanced → Network policy.
Alerts
Blocked connections appear in Detections with full context. If you’ve configured Slack, you’ll receive an alert for each incident. Learn more about Alerts.