Core concepts
Runs
Every execution produces a behavioral profile: process lineage, network egress, and assertion results.
Assertions
Runtime behavior as testable infrastructure. Assertions evaluate every run and surface verdicts in your workflow, just like a test suite.
Runtime Agents
Jibril, a lightweight eBPF runtime agent deployed in your execution environment. Captures process, network, and file activity at kernel level.
Get started
Quick Start
Generate a token, install a runtime agent, see your first run in minutes.
How it works
- Deploy Jibril, an eBPF runtime agent, in your execution environment
- Profile every outbound connection through process ancestry — traced back to the exact dependency that opened it
- Evaluate runtime assertions per run — verdicts surface in Step Summary, Slack, or webhooks
See it in action
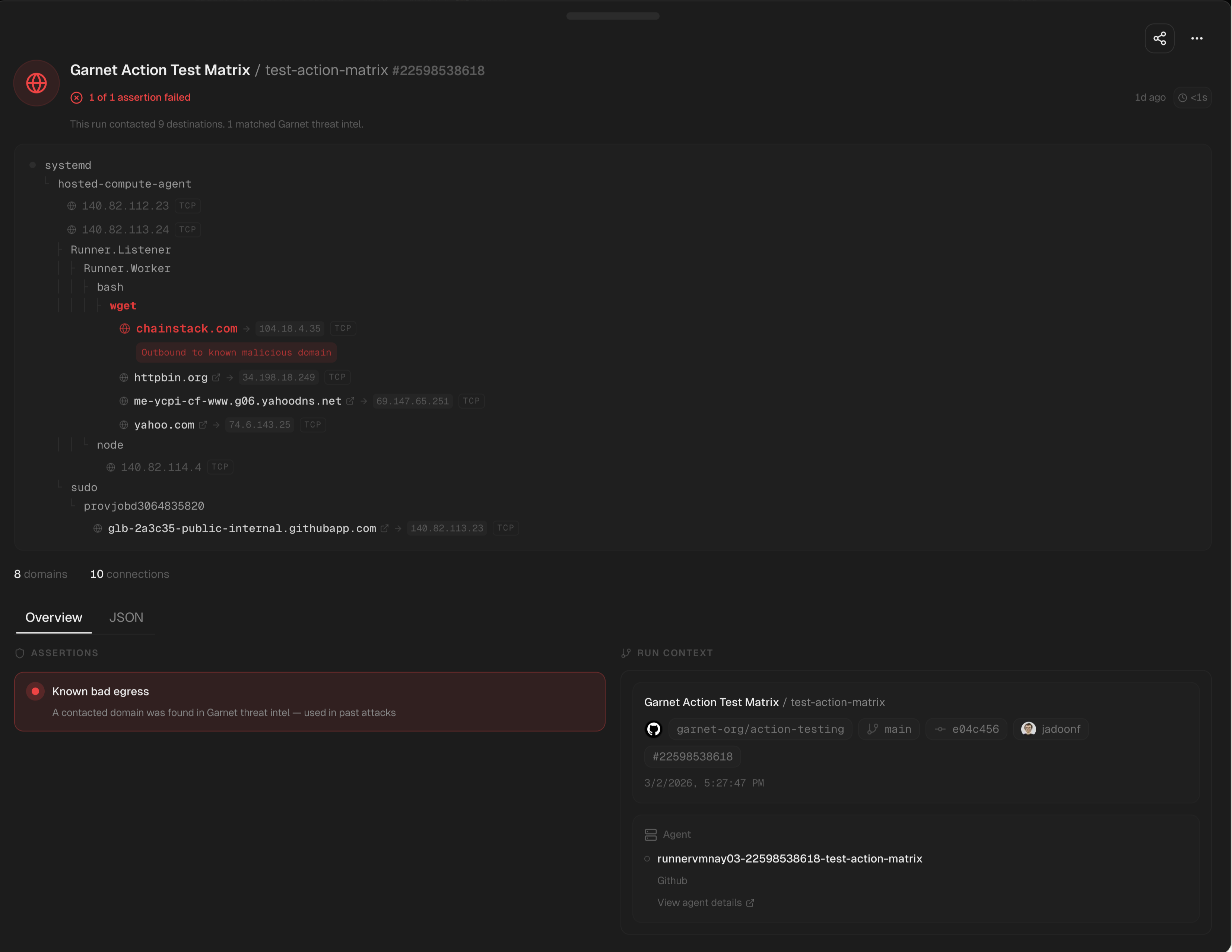
chainstack.com flagged as suspicious in this context — it was seen in past attacks through Garnet threat intel. The full process tree traces the connection back to wget inside the CI workflow.
Shai-Hulud v2 — Supply Chain Worm
See how Garnet detected a supply chain worm contacting suspicious domains during a live CI run