Why monitor Docker?
- Container breakouts and privilege escalation
- Malicious containers running crypto miners
- Supply chain attacks in Docker images
- Data exfiltration from containerized apps
- Resource abuse using host compute
Setup (2 minutes)
1. Get API token
2. Run Jibril container
3. Verify deployment
Configuration
Deployment modes
- Production (Recommended)
- Development
- Docker Compose
- Full threat detection
- Automatic blocking enabled
- Resource limits applied
- Auto-restart on failure
Advanced configuration
GARNET_MODE:production,development, orlightweightGARNET_BLOCKING:trueorfalseGARNET_LOG_LEVEL:debug,info,warn,errorGARNET_SCAN_INTERVAL: How often to scan (default:60s)GARNET_ALLOW_PATTERNS: Comma-separated patterns to ignore
What gets detected
Container Security
- Container escapes
- Privilege escalation
- Unauthorized mounts
- Runtime modifications
Network Threats
- C2 communications
- Data exfiltration
- DNS tunneling
- Port scanning
Resource Abuse
- Crypto mining
- Fork bombs
- CPU/memory abuse
- Storage exhaustion
Malicious Activity
- Malware execution
- Backdoor installation
- Credential theft
- File tampering
Verification
After deployment:- Check container status
- View logs
- Test container monitoring
- Visit dashboard - agent should appear within 2 minutes
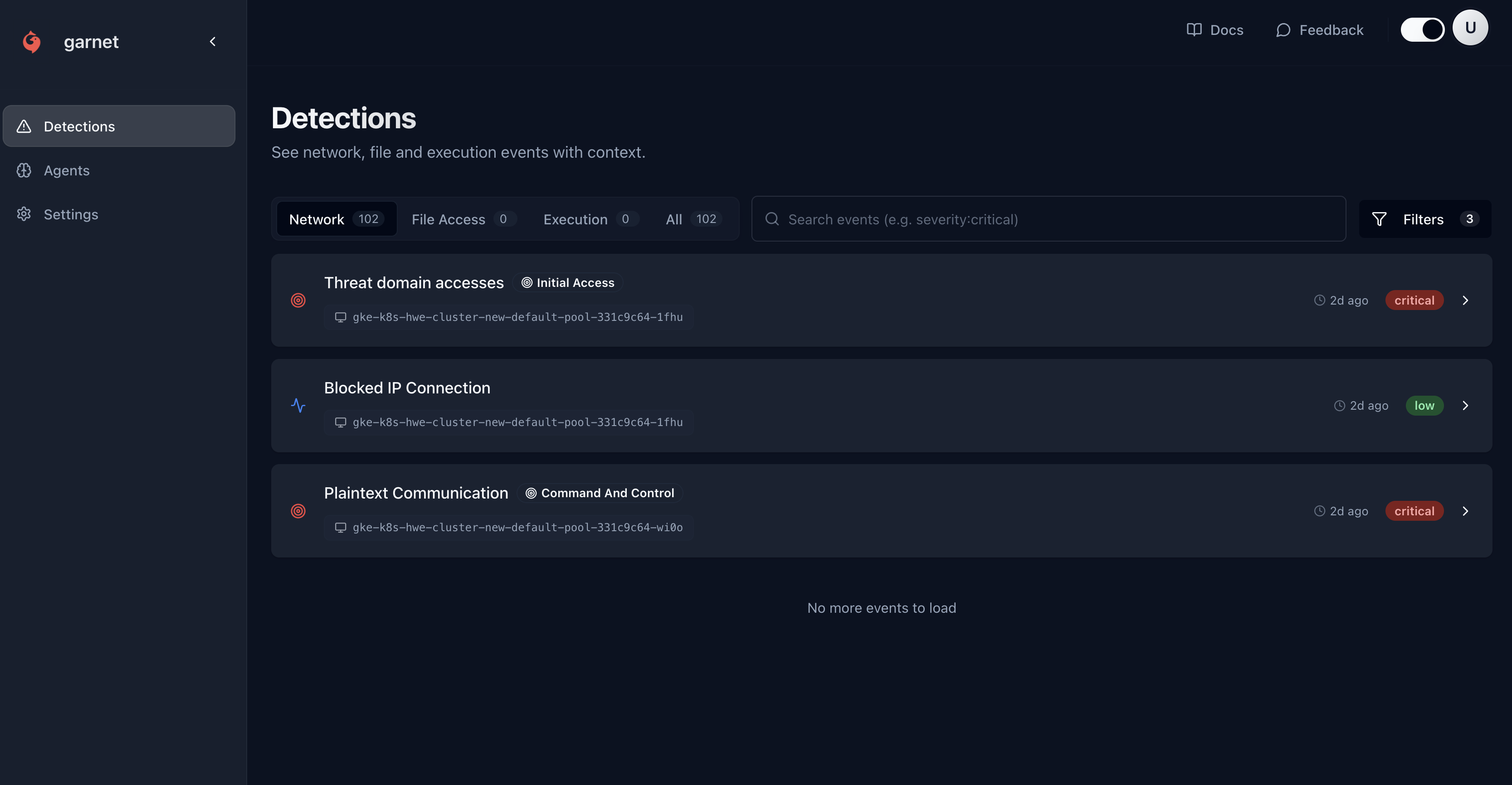
Example detections
Crypto miner in container
Container escape attempt
Management
Update Jibril
Monitor resources
View detailed logs
Troubleshooting
Container fails to start
Container fails to start
Symptoms:Fix:
- Check Docker version (needs ≥20.10):
- Verify host kernel version:
- Check container logs:
- Ensure privileged mode:
No agent in dashboard
No agent in dashboard
Wait 2-3 minutes for initial connection.If still missing:
- Check container logs:
- Test network connectivity:
- Verify API token:
- Test API access:
High resource usage
High resource usage
Symptoms: Host performance degradedSolutions:
- Set resource limits:
- Use lightweight mode:
- Increase scan interval:
Too many false positives
Too many false positives
Symptoms: Legitimate containers flagged as threatsFix: Add allowlist patterns:Or configure in dashboard: Settings → Policies → Add Allowlist