10-Minute Setup
Get Garnet running and see your first unknown egress detection in under 10 minutes.Prerequisites
- GitHub Actions
- Kubernetes
- Ubuntu runner (hosted or self-hosted)
- Write access to
.github/workflows/ - Repository secrets permission
Step 1: Get API Token
1
Sign in to Dashboard
Go to dashboard.garnet.ai and sign in.
2
Generate Token
Navigate to Settings → API Tokens and click Create Token.
3
Copy Token
Copy the token immediately—it won’t be shown again.
Step 2: Install Agent
- GitHub Actions
- Kubernetes
Add Garnet Action
Create or update.github/workflows/your-workflow.yml:Add Secret
- Go to Settings → Secrets and variables → Actions
- Click New repository secret
- Name:
GARNET_API_TOKEN - Value: Paste your token
- Click Add secret
Trigger Workflow
Push a commit or manually trigger the workflow to start monitoring.Detect-only by default. Garnet will observe and report unknown egress but won’t block anything yet.
Step 3: Generate Test Detection
Trigger a known-bad connection to verify Garnet is working.- GitHub Actions
- Kubernetes
Add a test step to your workflow:This will trigger an unknown egress event (safe—the domain doesn’t exist).
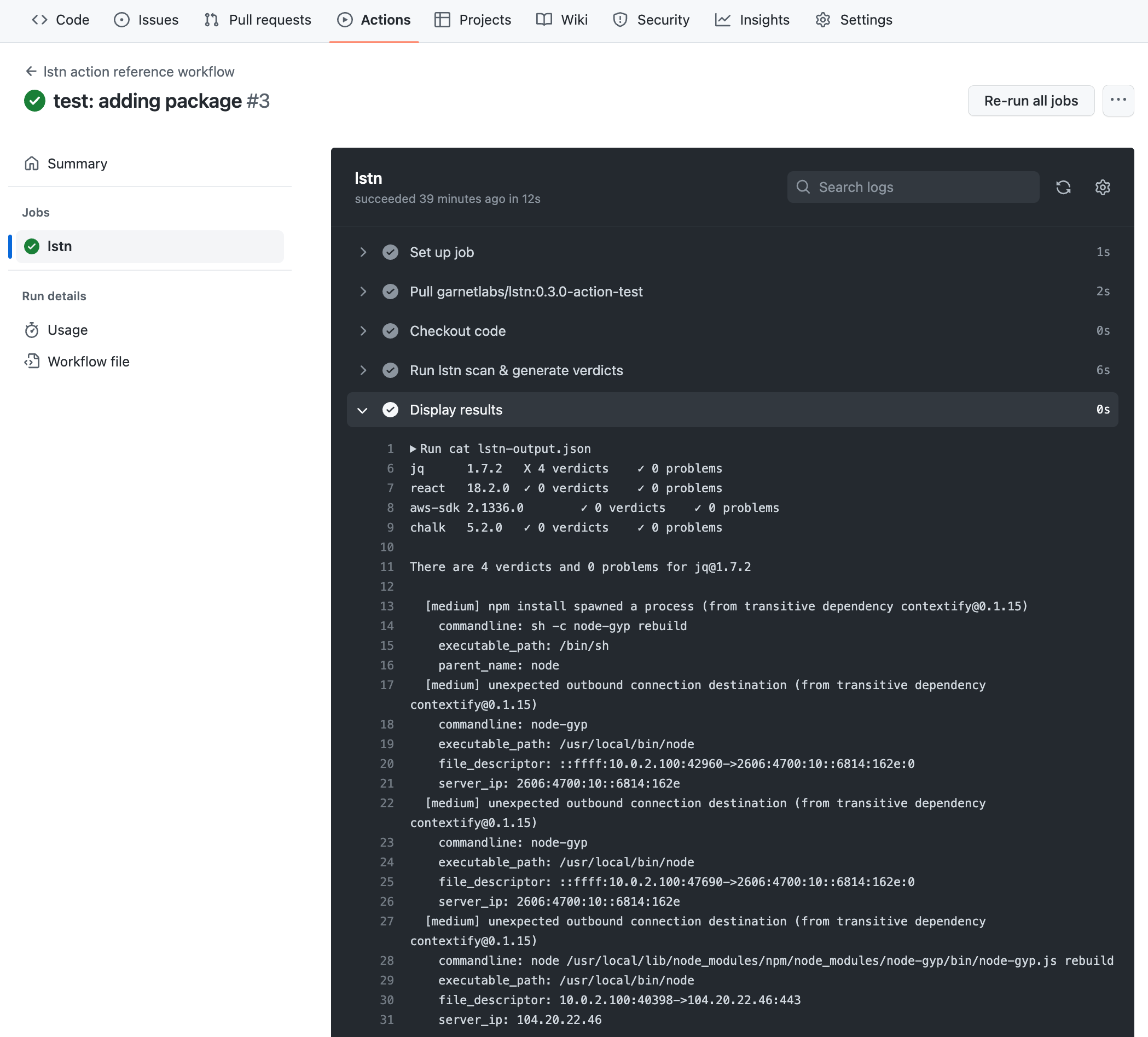
Step 4: View Your First Issue
1
Open Dashboard
2
Find the Issue
You should see an Issue for the unknown egress to
example-malicious-domain.com3
Inspect Details
Click the Issue to see:
- Process ancestry
- DNS query details
- Micro-context (workflow step or node)
Step 5: (Optional) Enable PR Comments
For GitHub Actions, enable automatic PR comments on unknown egress.Add Workflow Permission
Complete Example
What’s Next?
First Detection Checklist
Validate your setup and next steps
Enable Enforce Mode
Block unknown egress automatically
Troubleshooting
No Issues appearing
No Issues appearing
- Verify API token is correct in your secret/env var
- Check agent logs for “Connected to Garnet Platform”
- Ensure you triggered an actual outbound connection
GitHub Action step fails
GitHub Action step fails
- Verify
GARNET_API_TOKENsecret exists - Check runner is Ubuntu-based (not macOS/Windows)
- Review action logs for error messages
Kubernetes pods not starting
Kubernetes pods not starting
- Check privileged pod policy is enabled
- Verify nodes are Linux with kernel 5.8+
- Review pod events:
kubectl describe pod -n garnet