Events & Issues
Garnet collects Events (raw telemetry) and surfaces Issues (unknown egress detections).Events
Events are raw telemetry captured by Jibril agents via eBPF.Event Types
| Type | What It Captures | Example |
|---|---|---|
| DNS | Domain name queries | registry.npmjs.org |
| Connect | Outbound TCP/UDP connections | 104.16.132.229:443 |
| Process | Process start/exit with ancestry | node → npm → curl |
| File | File read/write correlated with network | /tmp/malware.sh |
Event Schema
Events are not alerts. Most events are normal—Garnet collects everything to build baselines.
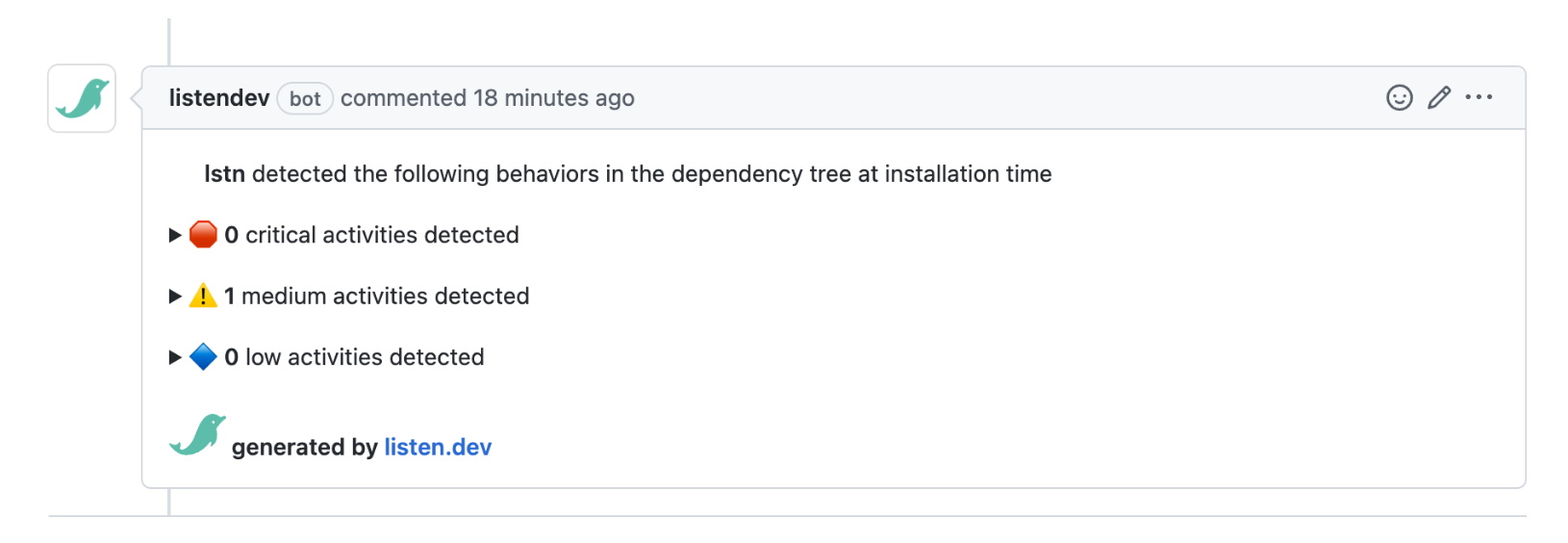
Issues
Issues are created when Garnet detects unknown egress: an outbound connection not seen in the baseline for that micro-context.Issue Lifecycle
Issue Fields
| Field | Description |
|---|---|
| Title | e.g., “Unknown egress to malicious-domain.com” |
| Severity | Critical, High, Medium, Low |
| Micro-Context | Workflow step (GHA) or Node (K8s) |
| Process | Full command line and ancestry |
| Domain/IP | Target of outbound connection |
| Verdict | Detected (logged) or Blocked (if Enforce enabled) |
| Timestamp | When the connection was attempted |
Example Issue
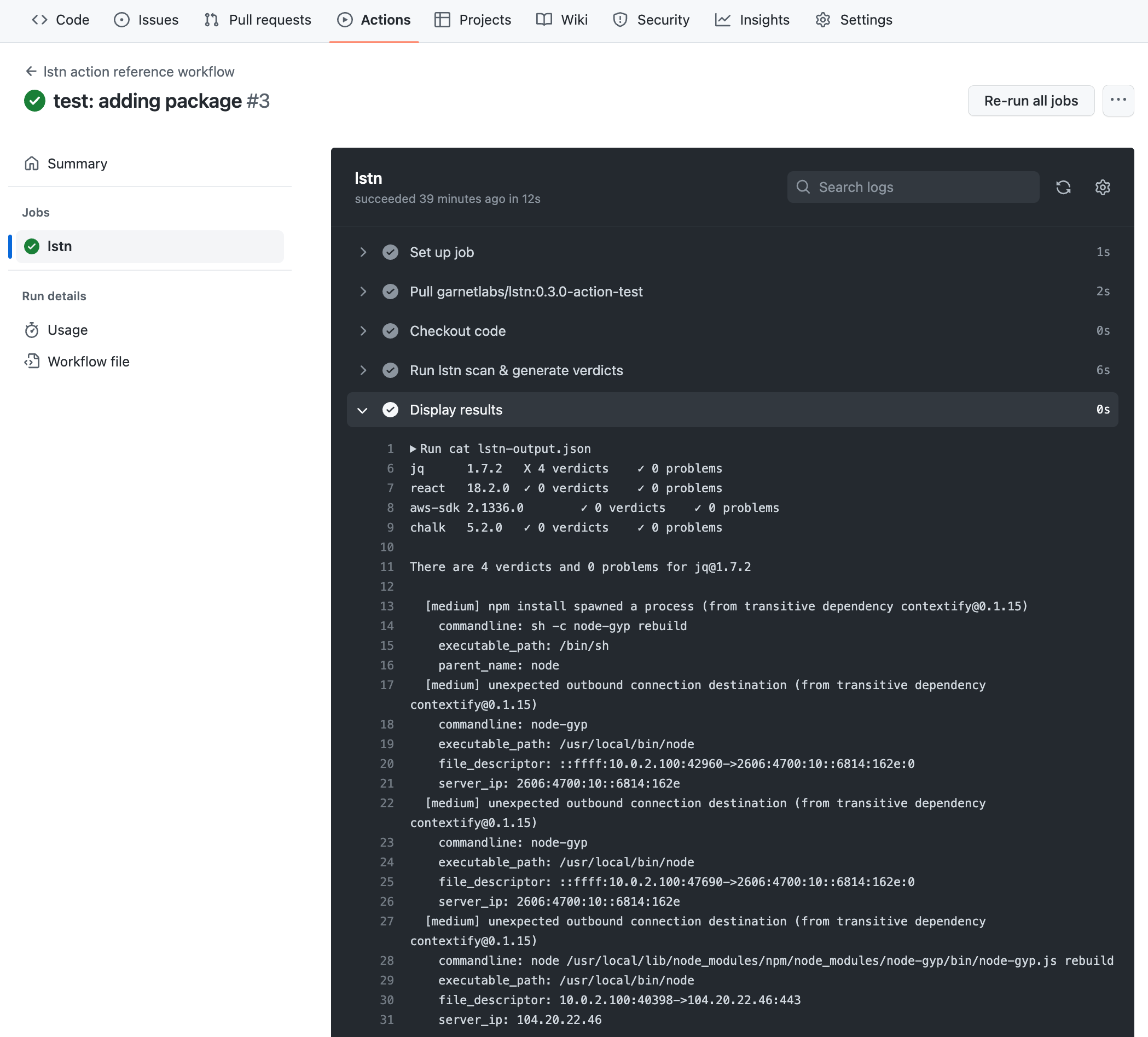
crypto-pool.example.com
Details:
- Process:
/usr/bin/xmrig --url=crypto-pool.example.com:443 - Parent:
sh→curl→xmrig - Context: Kubernetes node
gke-prod-node-123 - Verdict: Blocked (Enforce mode enabled)
How Baselines Work
Garnet learns “normal” behavior per micro-context over time.Micro-Context
A micro-context is a specific scope in which Garnet learns behavior:- GitHub Actions
- Kubernetes
Micro-context = Workflow + Job + StepExample:
- Workflow:
CI - Job:
build - Step:
Install dependencies
registry.npmjs.org once, future runs of this exact step expect it.But if step Run tests connects to registry.npmjs.org, that’s unknown egress (different micro-context).Baseline Learning Period
Garnet builds baselines automatically:- First run: All egress is new, but flagged as “establishing baseline”
- Next 7 days: Normal connections are learned
- After 7 days: Baseline is “stable”; unknown egress triggers Issues
You can adjust this. In Settings, configure baseline period from 1 to 30 days.
False Positives
What Causes Them?
- Dynamic infrastructure: CDNs with rotating IPs
- Vendor API changes: New endpoints added to third-party services
- Legitimate new dependencies: You added a new package
How to Handle
1
Review the Issue
Check if the domain/IP is expected for your workload.
2
Mark as Known Good
Dashboard → Issue → Mark as Known (adds to allowlist)
3
Add to Policy
Viewing Events & Issues
Dashboard
- Events: dashboard.garnet.ai/events — All raw telemetry
- Issues: dashboard.garnet.ai/issues — Unknown egress only
Filters
Filter by:- Severity: Critical, High, Medium, Low
- Verdict: Detected, Blocked
- Time range: Last hour, day, week, custom
- Context: Specific workflow, node, or cluster
Event Retention
| Plan | Retention |
|---|---|
| Free | 7 days |
| Team | 30 days |
| Enterprise | 90 days (configurable) |
Issues are retained forever, even if raw events expire.